Steganography
February 22, 2021
Throughout
history,
men have always sought to gain some advantage over other men. In the
Stone Age, a large
rock was better than a small
stone in
battle. Later, a
crossbow had the advantage over a traditional
bow and arrow. Advantage was also gained in
efficient transmission of
commands, and keeping those commands
secret from the
enemy.
Julius Caesar (100 BC-15 BC) used a simple
code, now called the
Caesar cipher, to maintain the secrecy of his
messages. In this code,
alphabet letters were shifted three places, with 'a' becoming 'd', a method called
substitution. At the end of the
alphabet, you needed to move to the start, with 'x' becoming 'a', etc.
Cryptography in the
digital age has advanced far beyond this, since
computers are very good at
breaking simple
ciphers.
Steganography is another method of secret communication. The word, “steganography,” is derived from the
Greek words στεγανός (steganos, "
covered or concealed"), and γραφή (graphia, "
writing"). As I wrote in my
children's book about secret codes, there's an interesting example of steganography in
ancient times.[1] A man's
head was
shaved, and a message was written on his bare head. When his
hair grew back, the message was hidden, and it was revealed when his head was again shaved.
As I wrote in an
earlier article (Watermark Ink, August 8, 2011), I wrote messages using "
invisible ink" as a child. You can write a message on
paper with
lemon juice, and the message is
invisible when the
liquid dries. Subsequent
heating of the paper by holding it over a
candle, or placing it in a hot
pan on a
cook stove, will cause the invisible message to appear. Although I did this myself as a child, this is one experiment in which
adult supervision is required. I didn't let my children do 90% of the things I did when I was a child!
The lemon juice invisible ink works because the
ascorbic acid in lemon juice decomposes at about 375°F, a little below the
memorable combustion point of
paper,
451°F. The presence of other
organic chemicals in the juice helps.
Milk works a little better than lemon juice. Its various
proteins and
fats decompose when heated to good effect (see figure).
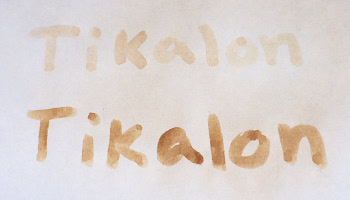
Invisible ink experiment.
The top line was written with lemon juice, the bottom with milk.
The writing was exposed by holding the paper a few inches above an electric stove heating element, but a safer option would be the use of a pan.
In our
modern age, it's more common for our
documents to be
digital, rather than paper. There is also a
plethora of
digital images; so, many techniques have been developed for hiding messages in digital images through slight variation of the
color codes. Images we see on most computers contain an amazing
16,777,216 different colors.
As a crude example of
image steganography, I wrote a
computer program in the
C programming language that converts a short
text file into
24-bit color color codes in which the message is encoded in the
red color channel (See figure.
source code here). These colors can be embedded as nearly invisible single
pixels in an image. This particular encoding is easily cracked by a skilled
cryptographer. However, variations of this, such as embedding the message with prior
encryption as changes in the
least-significant bits of the color encoding, are not.


![]()
Crude image steganography example. The image on the left shows the first paragraph of this article encoded as data in the red color channel. The image on the left shows single pixels of these colors overlaid on a NASA image of Jupiter. The encoding was done using a simple C language program (source code here). Note that this quickly coded program may contain some undetected errors. (Click for a larger version of the left image.. Magnifying this image on your web browser (multiple key presses of ctrl and + on my Firefox web browser) will reveal the pixels.)
The right image was created by using a rectangle size of 1x1 in the program, importing the resultant SVG image into the GNU Image Manipulation Program (GIMP), setting the background as transparent, and then overlaying the image with the Jupiter image. Note that saving images using lossy compression (as in JPEG), or shrinking images in size, will corrupt the message data.
Joab Kose,
Oscar Bautista, and
Vashish Baboolal of
Florida International University (Miami, Florida) have recently posted a short
review article about steganography techniques on
arXiv.[2] This article summarizes the methods for image steganography, and the similar idea of steganography in
audio files using essentially the same techniques.
Just as cryptography has its complementary discipline of
cryptanalysis, steganography has its
steganalysis. The easiest method is when a copy of the unmodified source file is available. The first check is a file
hash to determine whether or not the source file has been modified. Using the
Linux command line for my Jupiter example, above, we get the following:
md5sum -b Jupiter_raw.png
282a6ea7306e0dd7511c6005ecdaed34
md5sum -b Jupiter_with_data.png
71a99b5fb815e7bc44db1b57f4f07535
Now that we know that the source file has been modified, we can do an
XOR operation between
bytes of the files to see which bytes were modified. After that, standard cryptanalysis methods can be used on the digital data. I'm not a cryptographer, and this is an extremely simple example of something that can be quite difficult. As I once remarked to a
fellow scientist, "If it was easy, they wouldn't be paying us so much money to do it."[3]
The arXiv authors summarize the principal uses of steganography. These include
digital watermarking of image, audio, and
video files, moderately secure transmission of information that's not visible to unintended recipients, and a means by which
corporations can hide portions of
trade secret information. arXiv presently has more than 200 papers that have the word, "steganography," in their titles.
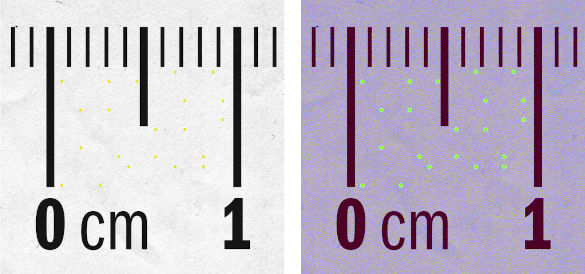
Printer Steganography - Yellow printer identification dots, barely visible, encoding the printing date, type of printer and printer identification. These are on every page printed by some printers. (Left image, a Wikimedia Commons image by Parhamr. The right image has been color processed by the GNU Image Manipulation Program (GIMP) to accentuate the dots. See ref. 4 for further information.[4]
References:
- Dev Gualtieri, "Secret Codes & Number Games: Cryptographic Projects & Number Games for Children Ages 5-16, Tikalon Press, December 20, 2014, 90 pp., ISBN:978-1942459019 (via Amazon).
- Joab Kose, Oscar Bautista, Vashish Baboolal, "Review and Test of Steganography Techniques," arXiv, December 15, 2020.
- Physicist PhD Salary, Economic Research Institute.
- The Electronic Frontier Foundation, Is Your Printer Spying On You?.
Linked Keywords: History; human; men; Stone Age; rock (geology); stone; battle; crossbow; bow and arrow; efficiency; efficient; military order (instruction); command; secrecy; secret; enemy; Julius Caesar (100 BC-15 BC); code; Caesar cipher; message; alphabet letter; substitution cipher; alphabet; cryptography; information Age; digital age; computer; cryptanalysis; code breaking; ciphers; steganography; Greek language; Greek word; hidden; covered; concealed; writing; child; children; book; ancient history; ancient times; head; shaving; shaved; hair; invisible ink; paper; lemon juice; invisibility; invisible; liquid; heat; heating; candle; cookware and bakeware; pan; cook stove; parental supervision; adult supervision; ascorbic acid; Fahrenheit 451; memorable; paper; 451°F; organic compound; organic chemical; Milk; protein (nutrient); fat; experiment; inch; electric stove; heating element; modern history; modern age; document; digital; plethora; digital image; RGB color model; color code; color depth; True color (24-bit); 16,777,216 different colors; image steganography; computer program; C programming language; text file; red color; channel (communications); image steg.c; source code; pixel; cryptography; cryptographer; encryption; least-significant bit; Jupiter's red spot; image steganography; paragraph; blog article; NASA image of Jupiter; software bug; undetected error; web browser; computer keyboard; key presses; control key ctrl; Firefox web browser; rectangle; SVG image; GNU Image Manipulation Program (GIMP); transparency; transparent; lossy compression; JPEG; data corruption">corrupt the message data; Joab Kose; Oscar Bautista; Vashish Baboolal; Florida International University (Miami, Florida); review article; arXiv; audio file format; steganalysis; hash function; Linux; command-line interface; Exclusive or; XOR; byte; colleague; fellow; scientist; digital watermarking; video; corporation; trade secret; yellow; printer identification dots; Machine Identification Code; Wikimedia Commons; Parhamr.