The Internet of Things that go Bump in the Night
February 29, 2016
As a young
scientist, I would often emulate the
photons of the
waveguides I studied by bouncing off the walls of the hallway between the
bedroom and
kitchen as I rushed to start my day. On one such trip, I accidentally nudged a
lever on the
setback thermostat for our
house, a fact I discovered the next
morning when I awoke to an unusually chilly
room. Well,
accidents happen, this one mildly affecting the four members of my
family that day, and the
fix took just a second.
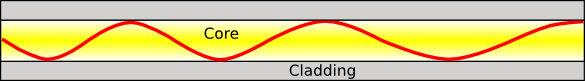
Light wave in a graded-index fiber. (Created using Inkscape.)
Some newer
thermostats are packed with much more
technology than my
mechanical thermostat. They're
Internet-connected, so they can be controlled anywhere using devices such as
smartphones. This sounds like a nice feature, but some owners of the
Nest smart thermostat found last month that the same problems that plague their
computers can affect their thermostat as well.[1]
The Nest thermostats are designed to automatically
update their software through the Internet, but an update caused a
battery drain in some devices that resulted in erratic behavior, or a complete shutdown resulting in no
heat on a cold
January day. Unlike the quick fix of my thermostat, some of the Nest units needed a total "
reboot." This involved unplugging the devices and manually restarting them. This high-tech tool with added
convenience turned out to be quite inconvenient.
Smart thermostats are an example of an emerging technology known as the "
Internet of Things (IOT)." The emergence of a new Internet addressing scheme called
IPv6 allows 2128 separately-accessible devices to be connected to the Internet. That's about 3.4x1038 addresses, or more than 1028 unique addresses for each person on Earth. By one estimate, there will be 50 billion devices connected to the Internet by 2020.[2] I wrote about the IOT in an earlier article (The Internet of Things, October 11, 2013).
Whether or not people really need an Internet-connected
toaster, it's
estimated that the IOT could increase the
U.S. gross domestic product by 2%-5% by 2025.[3] This economic benefit would arise from improved systems in
manufacturing, transportation, health care, and waste management.
As we've learned from our experiences with spam email,
computer hacking,
targeted advertising, and
individual tracking by smartphones and
electronic toll systems, Internet technology has a definite dark side. Similar problems will arrive with the IOT.
Economist,
Gérald Santucci, writes that that the present safeguards on information privacy are largely inadequate, and they threaten personal privacy and the rights of individuals as we progress to this "Internet of Everything."[3-4]

This memorable phrase from the 1986 remake of "The Fly," could be a motto for the Internet of Things. (Created with the GNU Image Manipulation Program, GIMP.)
Software developers continue in their attempts to secure the usual Internet devices against hackers and
corporate/
government snooping. As
this list shows, there are quite a few ways, such as the
man-in-the-middle attack, to hack your personal information. Along with these attack modes, IOT devices and devices using
RFID technology have additional problems that involve what are called
side-channel attacks.
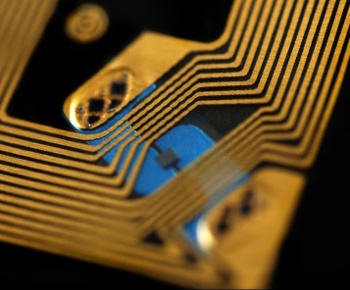
Portion of an RFID chip.
The gold wire loop serves as both an antenna and a means to extract power from the device that reads the chip's information.
(MIT image.)
In a side-channel attack, seemingly irrelevant details of device performance can lead to knowledge of its internal workings. These might be the time it takes to reject the wrong
password, or fluctuations in its power usage as it receives external commands. RFID devices are especially vulnerable to such attacks, since they are usually powered by the
reader device, and a rogue reader can play tricks with their power source as it attempts to discern the working of their internal software.
As
Chiraag Juvekar, a
graduate student in the
Department of Electrical Engineering and Computer Science at MIT, explains, side-channel extraction of things like passwords is difficult to do.
"The idea in a side-channel attack is that a given execution of the cryptographic algorithm only leaks a slight amount of information... So you need to execute the cryptographic algorithm with the same secret many, many times to get enough leakage to extract a complete secret."[5]
One way to thwart such attacks is to frequently change the
secret key used in sending and receiving
encrypted messages. A simplified scheme of this type is used in the
rolling code software for
vehicle keyless entry. However, a reader-powered device is vulnerable to an attack in which the reader repeatedly cuts the power before the chip changes to another secret key. This is an easy way to circumvent software that limits on the number of incorrect password entries before shutting down.[5]
People have been keeping secrets for a long time. This is a warded key from the 17th century, probably German. (Key image from the Walters Art Museum via Wikimedia Commons, modified.)
Juvekar is first
author on a
paper presented at the
2016 International Solid-State Circuits Conference,
San Francisco, that describes a side-channel safe RFID chip developed jointly by
MIT and
Texas Instruments.[5] The tactic that they used is to make certain that the chip always remembers its last state when power is removed. To do this, the
research team integrated
non-volatile memory into the
hardware.[5] The situation is
analogous to an interrupted
chess game when the
board pieces are left undisturbed so that play can resume again at any time.
The chips incorporate
ferroelectric crystal layers for two purposes. The first use is for
energy-storage capacitors so some operations can be continued when the external power source is removed. The second use is for a non-volatile memory that contains a record of the chip's last state. When external power is restored, the chip continues where it left off, including operations needed to change the key. It won't respond to external commands until this is done.[5]
The MIT RFID chip is somewhat slower than others, since it needs time to
charge its internal energy store before it accepts commands. The device, however, still gives thirty readings per second, which is sufficient for most RFID applications. Says
Ahmad Bahai,
chief technology officer at Texas Instruments,
"In the age of ubiquitous connectivity, security is one of the paramount challenges we face... Because of this, Texas Instruments sponsored the authentication tag research at MIT that is being presented at ISSCC. We believe this research is an important step toward the goal of a robust, low-cost, low-power authentication protocol for the industrial Internet."[5]
Some funding for this research came also from
Denso, a
Japanese automotive company.[5]
References:
- Jaikumar Vijayan, "Nest Issues Update to Fix Thermostat Glitches," eweek, January 11, 2016.
- Dave Evans, "The Internet of Things - How the Next Evolution of the Internet Is Changing Everything," Cisco Internet Business Solutions Group. April, 2011.
- Michael Mandel, "Can the Internet of Everything bring back the High-Growth Economy?" Progressive Policy Web Site, September 12, 2013.
- Internet of Things Demands New Social Contract To Protect Privacy, Security Ledger Web Site, September 19, 2013.
- Larry Hardesty, "Hack-proof RFID chips," MIT Press Release, February 3, 2016.
- Larry Hardesty, "Secure computers aren't so secure," MIT Press Release, October 30, 2009.
Permanent Link to this article
Linked Keywords: Scientist; photon; waveguide; bedroom; kitchen; lever; setback thermostat; house; morning; room; accident; family; maintenance, repair, and operations; fix; electromagnetic radiation; Light wave; graded-index fiber; Inkscape; thermostat; technology; programmable thermostat; clock thermostat; mechanical thermostat; Internet; smartphone; Nest Labs; smart thermostat; computer; patch; software update; battery; heat; January; reboot; convenience; Internet of Things; IP address; Internet addressing; IPv6; Earth; toaster; approximation; estimate; United States; U.S.; gross domestic product; economy; economic; manufacturing; transportation; health care; waste management; spam email; computer hacking; targeted advertising; GPS tracking; individual tracking; electronic toll system; economist; Gérald Santucci; information privacy; 1986 remake of "The Fly"; motto; GNU Image Manipulation Program, GIMP; Software developer; corporation; corporate; government; mass surveillance; snooping; list of cryptographic attacks; man-in-the-middle attack; radio-frequency identification; RFID; side-channel attack; integrated circuit; chip; gold; electromagnetic coil; wire loop; antenna; electric power; password; RFID reader; Chiraag Juvekar; postgraduate education; graduate student; Department of Electrical Engineering and Computer Science at MIT; cryptography; cryptographic; algorithm; secret key; encryption; encrypted; rolling code; remote keyless system; vehicle keyless entry; secrecy; secret; warded lock; warded key; 17th century; Germany; German; Walters Art Museum; Wikimedia Commons; author; academic publishing; paper; 2016 International Solid-State Circuits Conference; San Francisco; Massachusetts Institute of Technology; MIT; Texas Instruments; research; non-volatile memory; hardware; analogy; analogous; chess game; board pieces; ferroelectricity; ferroelectric; crystal; epitaxy; layer; energy-storage; capacitor; charge; Ahmad Bahai; chief technology officer; authentication; authentication protocol; industry; industrial; Denso; Japan; Japanese; automotive company.