Cryptography for Kids
January 12, 2012
I'm amazed that I survived my
mathematics education. My first memory of math is learning how to "properly" write the number two. The teacher wanted us to write it with a little loop at the bottom; I had learned to write it from my father in the way that it appears in print; that is, "2." Why there was a problem, I still don't know.
My next memory was our
memorization of the
multiplication table. Yes, that knowledge is very useful, but for a child, very boring. I had trouble with (8 x 9), until I realized that it's just (8 x 10) - 8. Much elementary mathematics is boring, so how you can make mathematics interesting to children?
Children love
keeping secrets. As a child, one of my favorite
chemistry experiments (if it can be called that) was writing with
invisible ink. I wrote about this in a
previous article (Watermark Ink, August 8, 2011). That article includes some
recipes you can share with your children with suitable adult supervision (see figure). Nowadays, this exercise is called
steganography, and it's applied to
digital images, also.
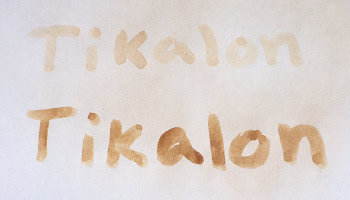
Invisible ink
The top line was written with lemon juice, the bottom with milk. The writing was exposed by holding the paper a few inches above an electric stove heating element)
Today,
electronic circuitry is quite inexpensive, and digital secret-keeping technology has been applied to children's toys. One intereting example of this is the Radica Girl Tech Password Journal Electronic Diary that I've seen in
television commercials. You can view a
YouTube video of one of these commercials,
here. This diary unlocks to a spoken password, and a
patent application on the concept has been filed by Radica.[1]
Obviously, the
algorithm used in a toy must be quite simple, which leads to an interesting
science fair type of project. Using
speech synthesizers available as
free-open-source-software (FOSS), you can try to tailor the synthesized voice to break the password protection. This is somewhat like what
Spock did in the
Star Trek episode,
The Menagerie, when he synthesized
Kirk's voice to hijack the
Enterprise.
One possible means of secret messaging is the
codebook in which words are replaced by
symbols. The
Alchemists did this, using symbols for the
elements.
Chemists today do the same thing using the letter abbreviations for the elements. There's not much secrecy in that anymore, unless you try to explain why
tungsten is "W" and
antimony is "Sb."
Physicians have their own codes, using
Greek and
Latin nomenclature. They go a further step in
obfuscation by using
abbreviations. Thus, in
prescriptions,
p.o.,
per os, means by mouth, and
q.h.s.,
quaque hora somni, means every night at bedtime.
In an effort to interest children in careers in
cryptography, the
US National Security Agency has a web site called
CryptoKids®.[2] The web site has a variety of games and puzzles suitable for children through
high school age, including the following "brainteaser" that requires high school level
algebra:
The difference of two positive numbers is 1. The product of these same two numbers is also 1. What is the difference of the cubes of these two numbers?[3]
The Crypto Kids include the two interesting chatacters shown below.
T. Top® character from NSA CryptoKids web site.
T. Top is a computer scientist.
Image provided Courtesy of the National Security Agency)
![]()
Slate® character from NSA CryptoKids web site.
Slate is a mathematician. The allusion to Ronald Graham is apparent.
Image provided Courtesy of the National Security Agency)
I've written an online secret message program for children that can be found
here.[4] A phrase of up to 25 characters can be entered, and the result is a
PDF file that contains a page of
random characters with the phrase embedded in it, and a second mask page. When the mask is laid over the first page, the phrase appears through the holes.
This implementation is definitely not what you would call cryptographically secure, but it's great fun for children; and it proves that I can still write code - The
computer kind, that is.
References:
- Laureen A. Trotto, Maureen T. Trotto, Rober A. Ruginis and Robert W. Jeffway, "Interactive Multimedia Diary," US Patent Application 20070124673, May 31, 2007.
- CryptoKids® Web Site, US National Security Agency.
- Answer: Y is (-1 + √5 )/2; X=(1 + √5)/2; the difference of the cubes is four.
- Secret Message Program from Tikalon. This program has been tested with FireFox 3.6.24, Google chrome 16.0.912.63 and Internet explorer 8, version 8.0.60001.18702. Thanks to Mike Gualtieri of Kiddix Computing and Steve Sund for checking the compatibility for PDF on their web browsers.
Permanent Link to this article
Linked Keywords: Mathematics education; memorization; multiplication table; secrecy; keeping secrets; chemistry; experiment; invisible ink; watermark; recipe; steganography; digital image; lemon juice; milk; electric stove; electronic circuitry; television commercial; YouTube; patent application; algorithm; science fair; speech synthesizer; free-open-source-software; FOSS; Spock; Star Trek; The Original Series; The Menagerie; Kirk; Enterprise; codebook; symbol; Alchemist; element; chemists; tungsten; antimony; physicians; Greek; Latin<; nomenclature; obfuscation; abbreviations used in medical prescriptions; prescription; cryptography; US National Security Agency; CryptoKids®; high school; algebra; NSA CryptoKids web site; Ronald Graham; random; source code; US Patent Application 20070124673; US National Security Agency; Kiddix Computing.